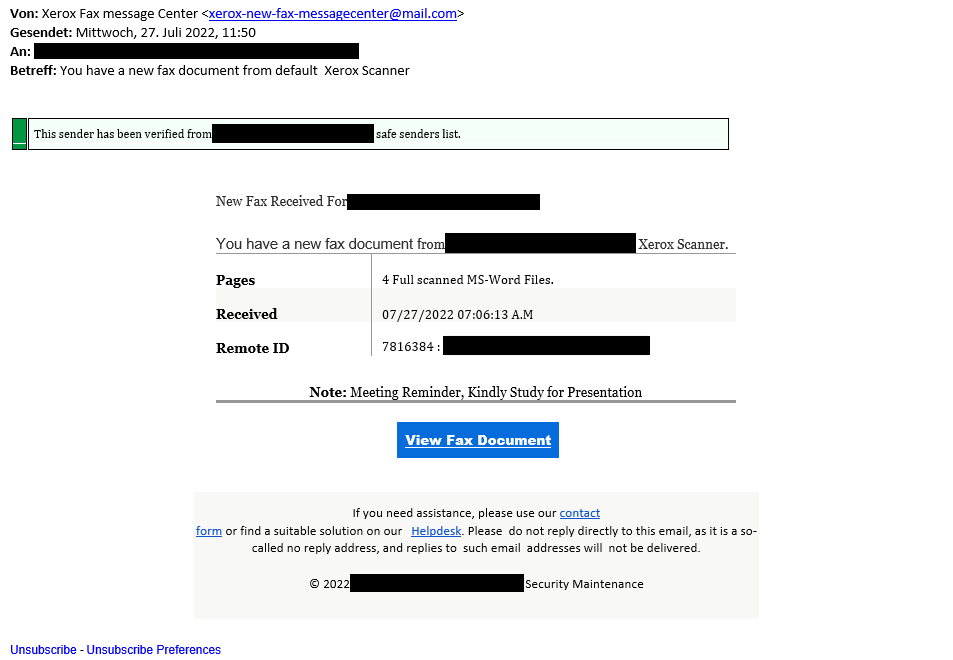
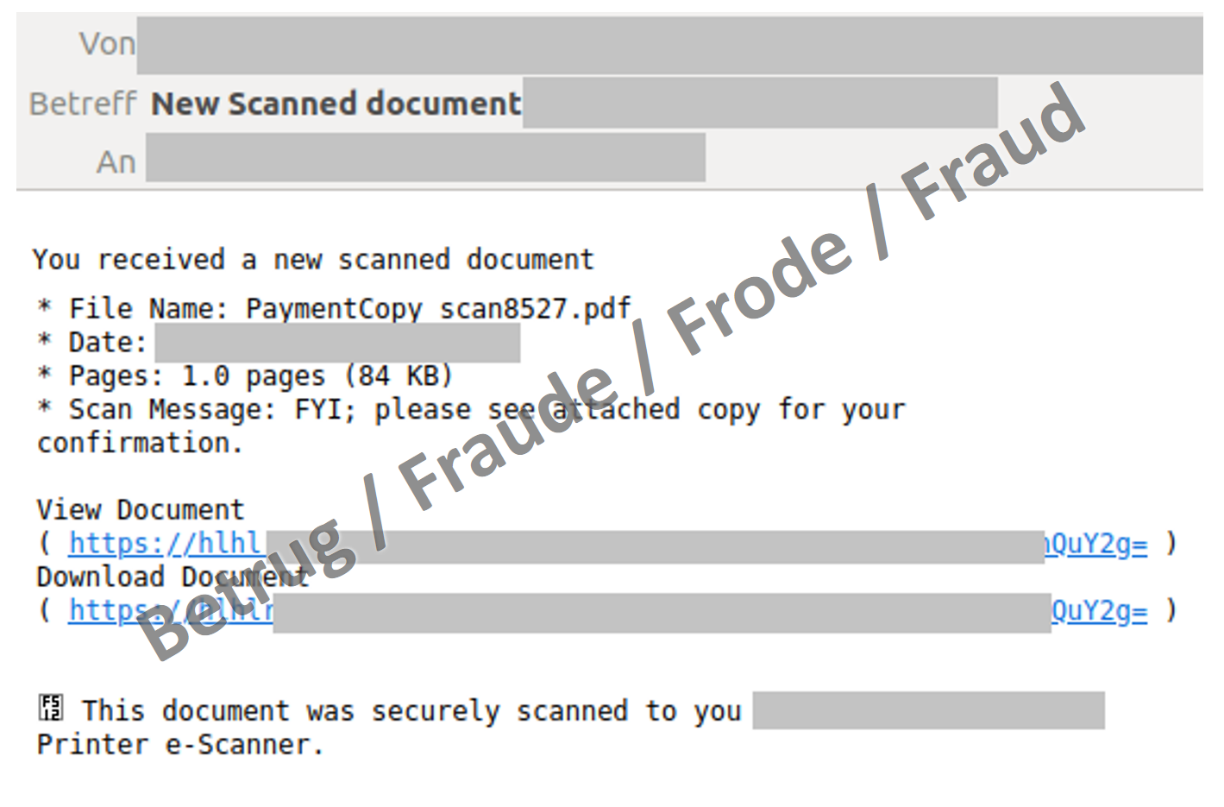
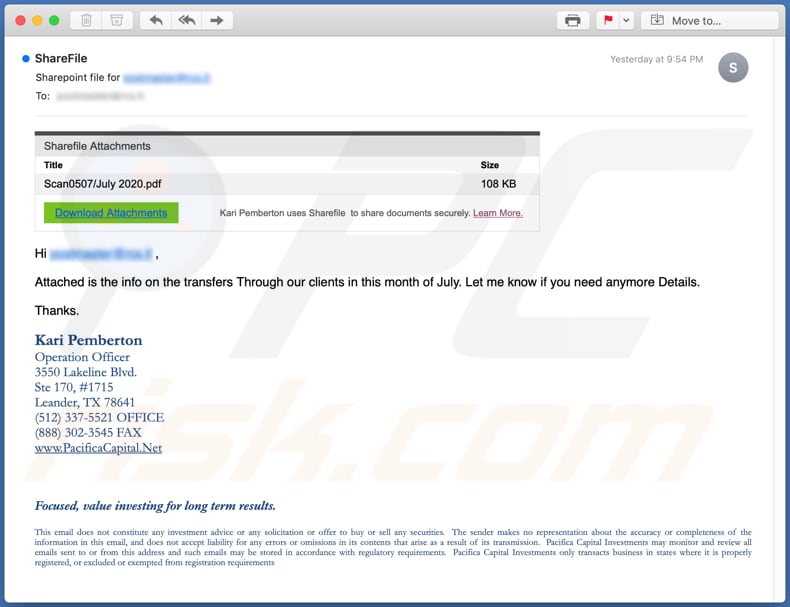
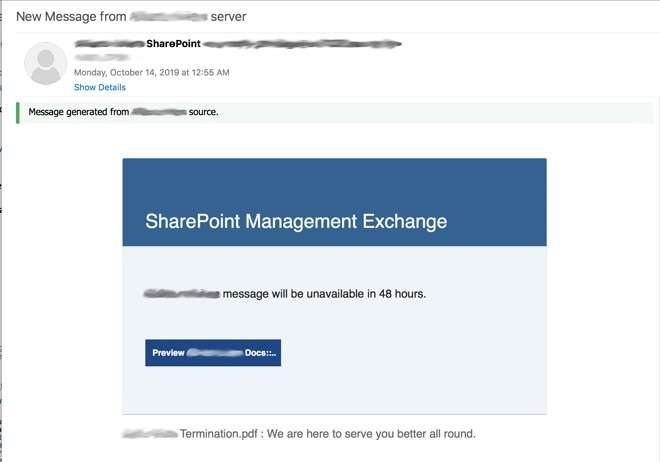
Sécurité Internet Cybersécurité Scanner D'empreintes Digitales Reconnaissance Faciale Mot De Passe Icônes De Phishing Modèle De Mise En Page De Conception Infographique Concept De Présentation Créative Avec 5 étapes | Vecteur Premium
Vecteur Stock Internet Security, cyber security, fingerprint scanner, face recognition, password phishing, icons Infographic design template. Creative concept with 5 steps | Adobe Stock